🔐 Stacktic Security Framework Documentation
📋 Table of Contents
- Executive Summary
- Introduction
- Chapter 1: Network Security
- Chapter 2: Access Control
- Chapter 3: Policy Enforcement
- Chapter 4: Traffic Management
- Chapter 5: Data Protection
- Chapter 6: Compliance & Governance
- Chapter 7: Source Code Security
- Key Takeaways
📝 Executive Summary
Stacktic provides an automated, metadata-driven security framework that transforms complex security implementations into simplified, manageable processes. This document outlines how Stacktic automates security from infrastructure protection to policies and RBAC, ensuring enterprise-grade security with minimal manual effort.
🎯 Introduction
Why Stacktic Security Framework?
Stacktic is designed to automate security—from infrastructure protection to policies and RBAC. As a metadata-based solution, Stacktic understands stack layers and can automatically deploy and enforce security best practices.
Core Security Principles
- 🔄 Automation First: Security configurations generated automatically
- 🧩 Metadata-Driven: Intelligent security based on stack relationships
- 🛡️ Defense in Depth: Multi-layered security approach
- 📊 Continuous Compliance: Real-time auditing and reporting
Chapter 1: Network Security
1.1 🛡️ Network Policies and Micro-Segmentation
The Challenge
In real-world Kubernetes environments, NetworkPolicies are rarely used to their full potential because:
- ❌ They're complex to manage
- ❌ Many security teams apply policies only at the cluster level, not at the stack level
- ❌ Micro-segmentation—isolating traffic between stack layers—is challenging and often avoided
The Stacktic Solution
Stacktic automates this complexity by:
- ✅ Analyzing link directions and metadata to generate hundreds of NetworkPolicies automatically
- ✅ Delivering out-of-the-box micro-segmentation in minutes—work that would normally take months
- ✅ Creating granular policies at the stack layer level
Implementation Example
# Example: Generated NetworkPolicy structure
tree networkpolicy | wc -l
3146
# Sample generated policies:
├── networkpolicy__test__strimzi__all__strimzi__egress__ports__strimzi__nr101__lines15.yaml
├── networkpolicy__test__strimzi__all__strimzi__ingress__ports__strimzi__nr100__lines15.yaml
├── networkpolicy__test__strimzi__exception__system__egress__ports__443__nr36__lines18.yaml
├── networkpolicy__test__strimzi__to__minio__egress__ports__9000__nr70__lines18.yaml
└── networkpolicy__test__strimzi__to__postgresql__egress__ports__5432__nr71__lines18.yaml
⚠️ Best Practice: Test and apply these policies in staging first. If your source code or images communicate outside the relationships defined in Stacktic metadata, the application may break. This is expected behavior for the highest security level.
Chapter 2: Access Control
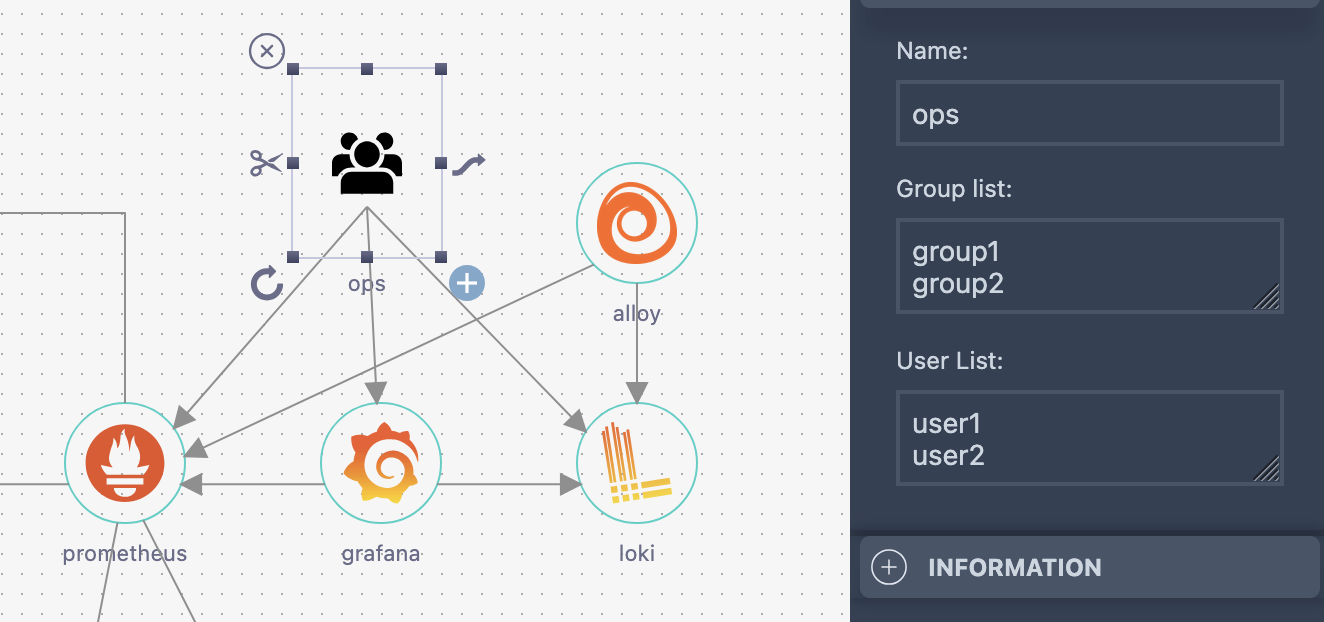
2.1 👥 RBAC Simplified
The Three-Layer RBAC Approach
RBAC (Role-Based Access Control) can be difficult to manage. Stacktic addresses this using a three-layer approach:
| Layer | Description | Benefit |
|---|---|---|
| 1. Component-Level RBAC | Enabled by default on every component | Automatic service account management |
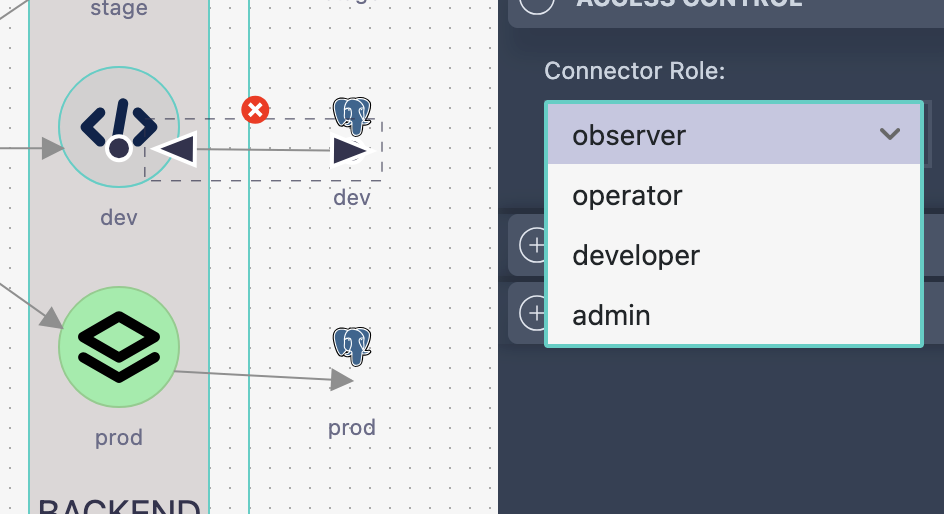
| 2. Link-Level RBAC | Relationships between source code and components | Auto-generated app-level permissions |
| 3. User-Level RBAC | Direct user/group to component linking | Simplified kubectl access management |
Key Features
- 🔐 Automatic Service Account Creation
- 🔗 Relationship-Based Permissions
- 👤 Intuitive User Management
- 📝 Maintainable Configuration
USER LEVEL RBAC
APP RELATION LEVEL RBAC
Chapter 3: Policy Enforcement
3.1 📜 OPA (Open Policy Agent) Integration
Overview
OPA is central to Stacktic's security enforcement, providing policy-as-code capabilities.
Core Capabilities
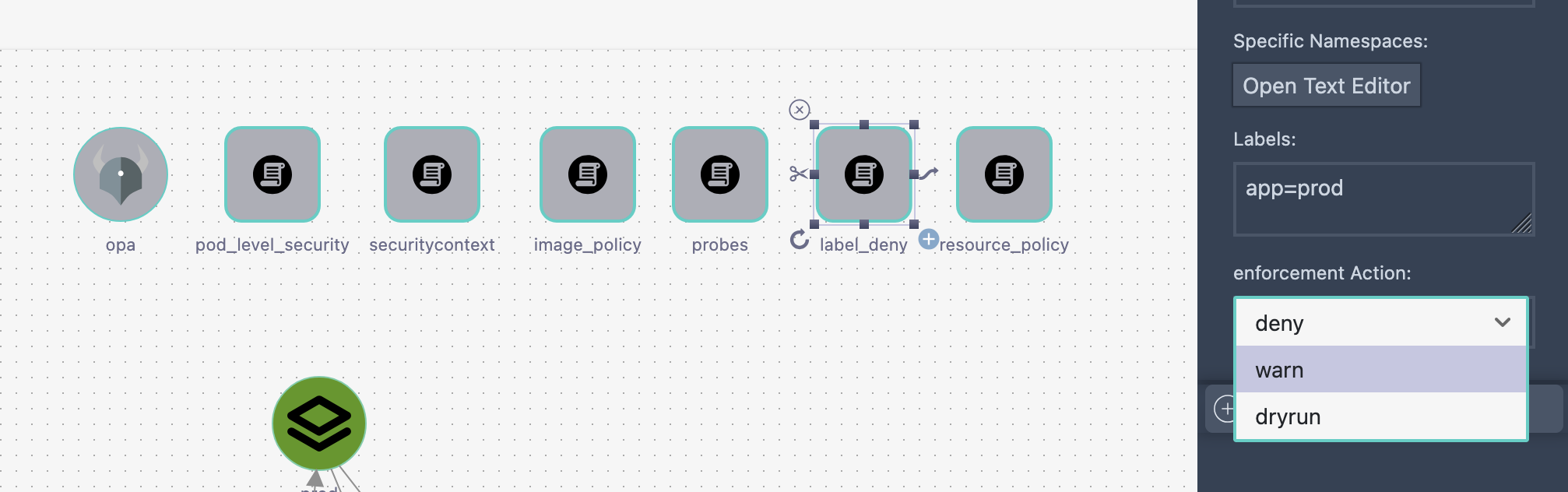
Policy Automation
- ✅ Automate policies using labels or namespaces
- ✅ Choose between Dry Run and Enforce modes
- ✅ Dynamic policy testing based on environment
Example Workflow
1. Add securityContext → Check labels
2. Label source code → Apply policies
3. Integrate metadata → Generate audit reports
Advanced Features
| Feature | Description |
|---|---|
| Dynamic Testing | Automates tests based on test environment |
| LiveView Integration | True/false insights directly in UI |
| Source Code Tuning | Adjusts code to meet OPA policies |
💡 Tip: Keep security definitions inside Stacktic to maintain full audit and reporting capabilities. External labels or policies may not appear in audit reports.
Chapter 4: Traffic Management
4.1 🌐 Traffic Security
Layer 7 Security Management
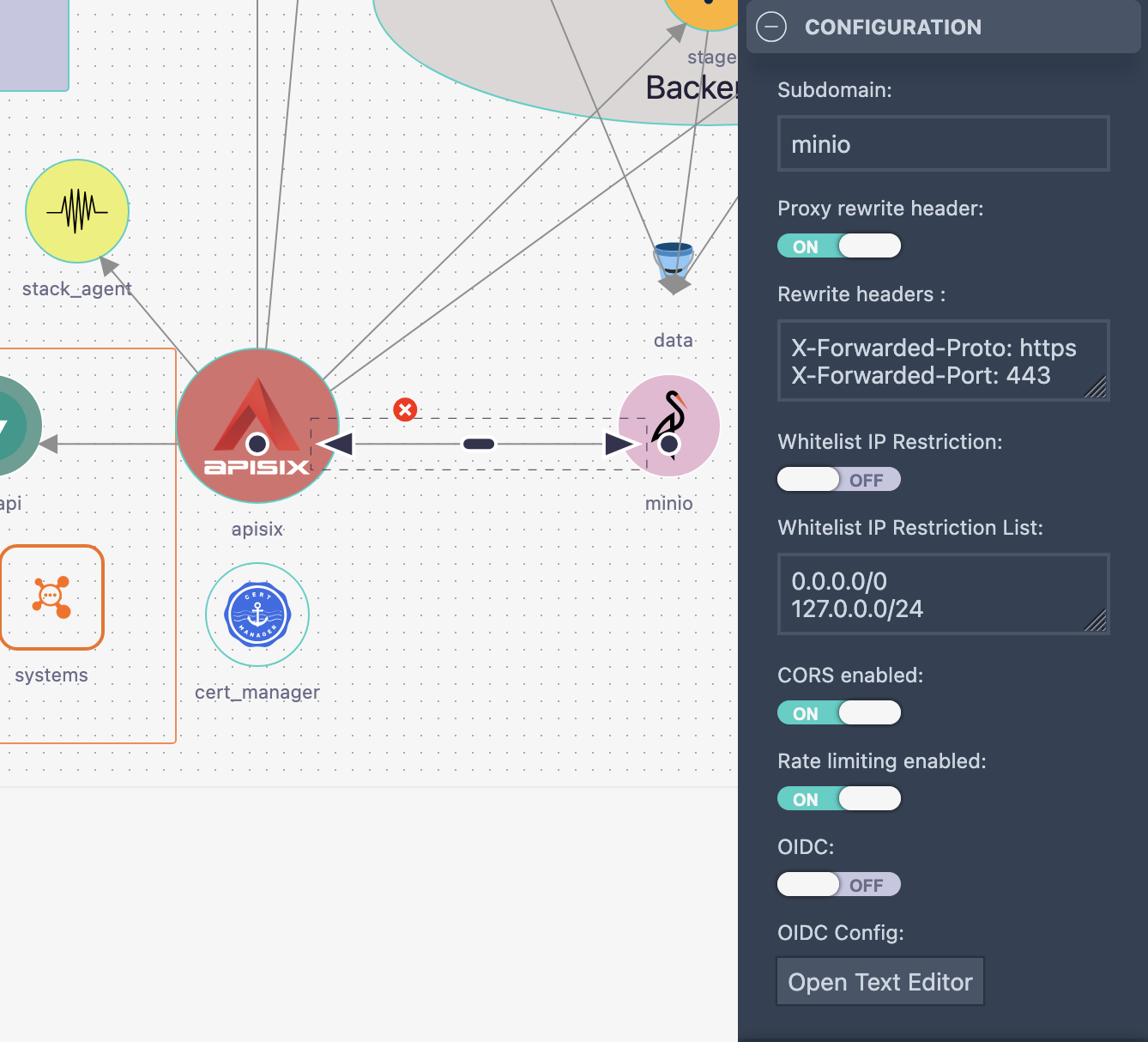
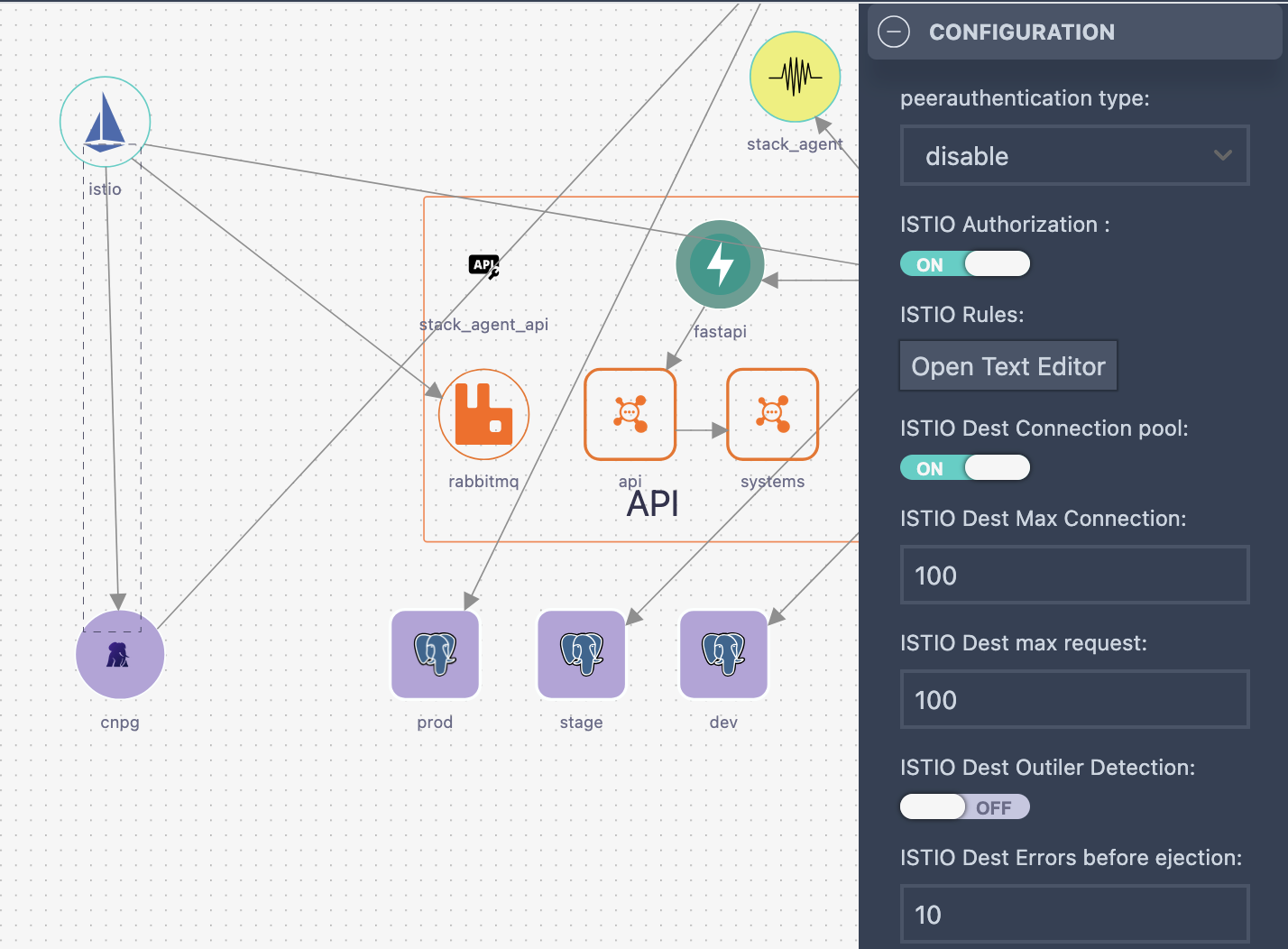
Traffic security is managed through components like Istio or APISIX. Stacktic abstracts complex configurations into links and attributes.
Key Capabilities
- 🚦 Traffic Control
- Block, route, or control traffic at Layer 7
- Limit traffic to specific routes or IP ranges
- 🔐 Authentication
- OIDC integration (e.g., Keycloak)
- mTLS between services
- 🔄 Traffic Policies
- CORS configuration
- URL rewriting rules
- Rate limiting
- 🔄 Links your Services Mesh
- Full Mesh in minutes
- Add rules, and specific configuraiton per link
- Centrelized Mesh control
Chapter 5: Data Protection
5.1 🔒 Secrets Management
Comprehensive Secret Lifecycle
Stacktic provides enterprise-grade secrets management with multiple layers of protection.
Core Features
Default Protection
- ✅ All environment variables saved as Kubernetes secrets
- ✅ Automatic secret rotation capabilities
- ✅ Version-controlled secret management
Advanced Security (SOPS Integration)
Features:
- Encrypt secret files in public repositories
- Decrypt only with appropriate keys
- Full lifecycle management:
• Rotate secrets
• Update configurations
• Re-encrypt on demand
Secret Management Workflow
- Create → Environment variables automatically secured
- Encrypt → SOPS encryption for repository storage (optional)
- Deploy → Secrets injected securely at runtime
- Rotate → Automated rotation without disruption
- Audit → Full tracking and compliance reporting
This ensures secrets remain secure, manageable, and version-controlled throughout the entire stack lifecycle.
Chapter 6: Compliance & Governance
6.1 📊 Security Audits and Reports
Comprehensive Reporting
Every configuration and status generated by Stacktic is translated into comprehensive audit reports.
Report Features
| Report Type | Content | Use Case |
|---|---|---|
| Configuration Analysis | Policy conflicts, misconfigurations | Pre-deployment validation |
| Security Posture | Overall security score and gaps | Executive reporting |
| Compliance Report | Standards adherence (CIS, PCI-DSS) | Audit preparation |
| Change Tracking | Configuration drift detection | Continuous monitoring |
Benefits
- 📈 Validate compliance continuously
- 🔍 Identify security gaps proactively
- 📋 CISO-grade reporting out of the box
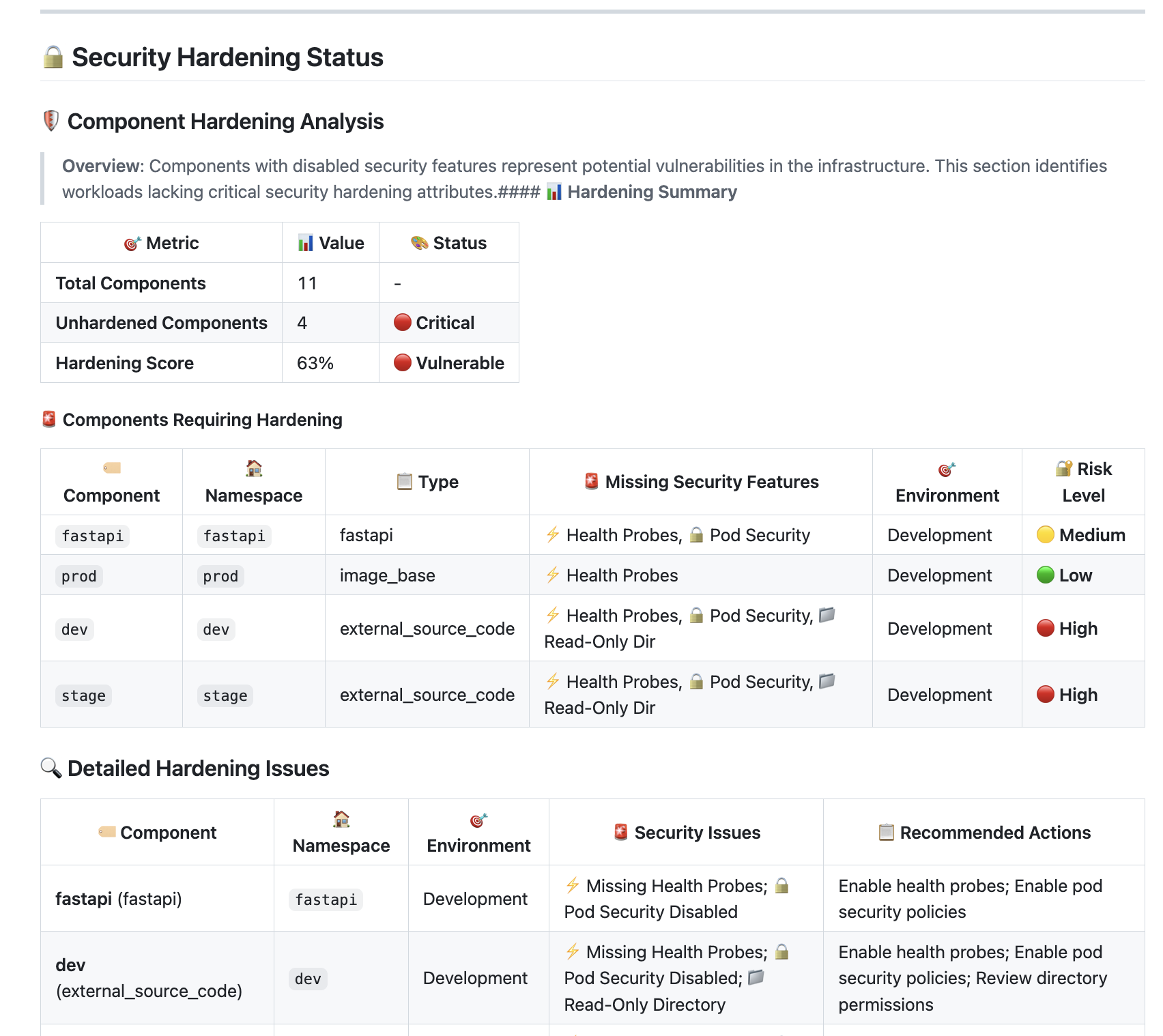
Chapter 7: Source Code Security
7.1 🔍 Code Security
Overview
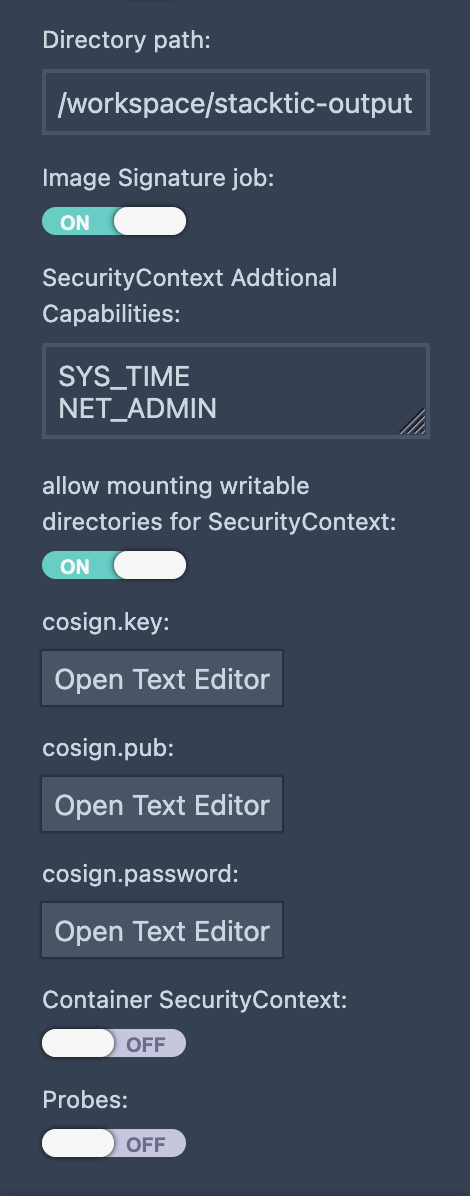
Stacktic provides pre-defined configuration for the container and image level security
Key Features
- ✅ tune your level security: switch on sec, add allowed directories.
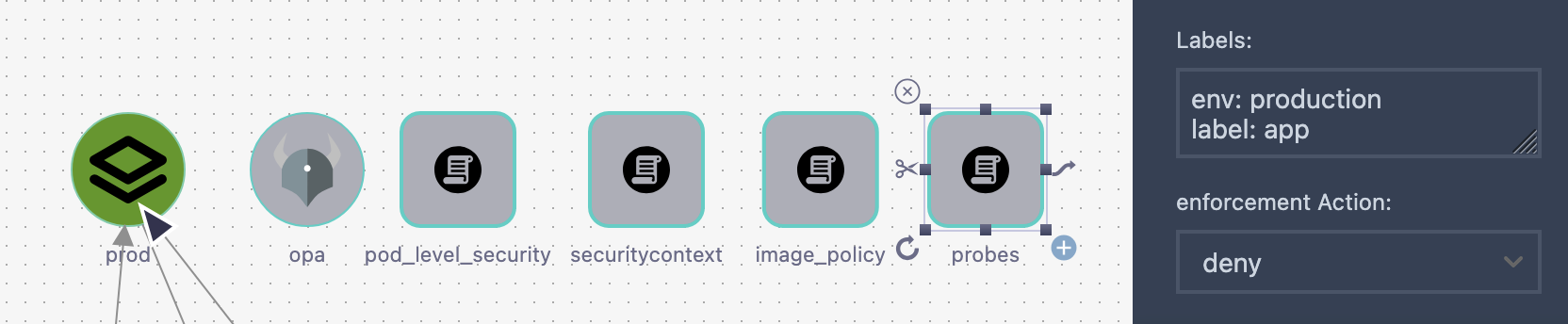
- ✅ Enable OPA validation: IEnforce OPA to validate your source codee configuration
- ✅ Audit report: Audit report will identify the source code security level of the full stack
identify missing Policies
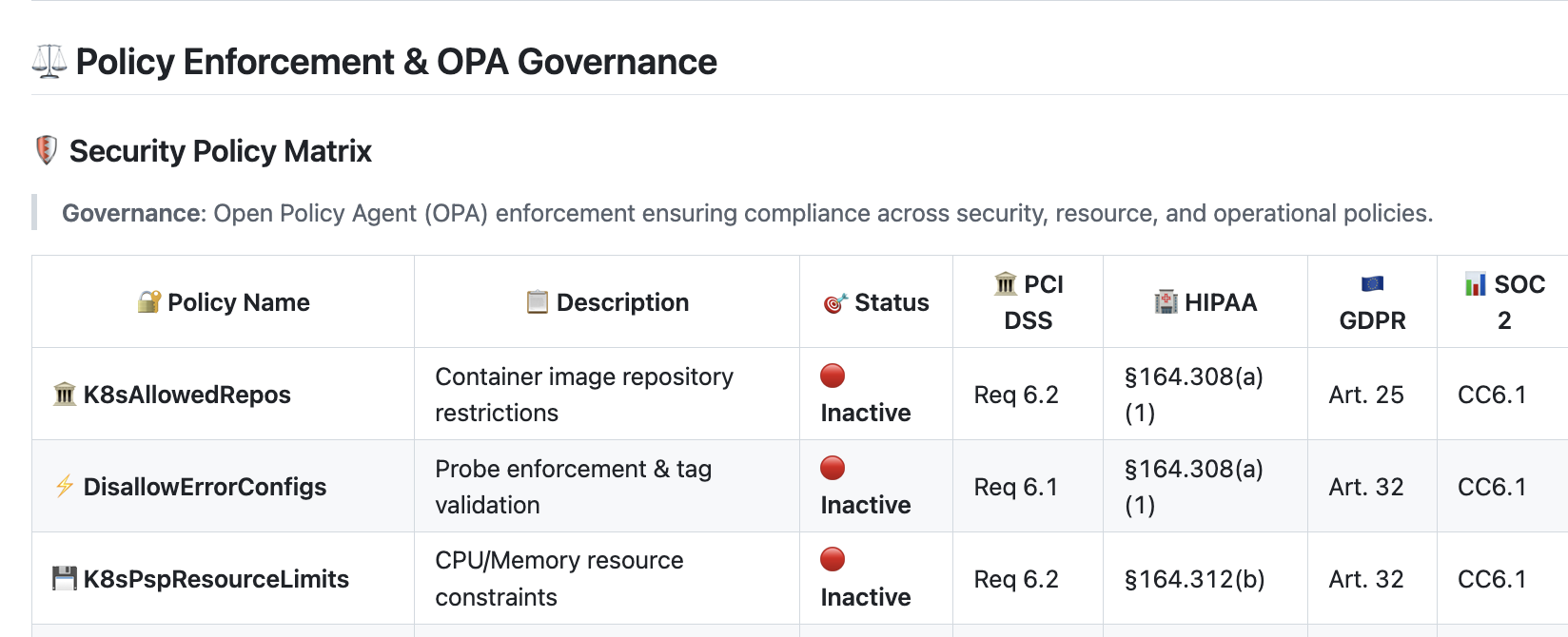
identify missing Source code Security
🎯 Key Takeaways
What Stacktic Security Framework Delivers
| Feature | Traditional Approach | Stacktic Approach | Time Saved |
|---|---|---|---|
| Network Policies | Manual creation, months of work | Auto-generated from metadata | 95% |
| RBAC Setup | Complex role definitions | Three-layer automation | 80% |
| OPA Policies | Manual policy writing | Template-based automation | 70% |
| Traffic Security | Complex Istio/APISIX configs | Abstracted link attributes | 85% |
| Security Audits | Manual assessment | Continuous automated reports | 90% |
| Secrets Management | Multiple tools needed | Integrated lifecycle | 75% |
Summary Benefits
✅ Automated Security: Minimal manual configuration required
✅ Compliance Ready: CISO-grade reports out of the box
✅ Best Practices: Enterprise security patterns by default
✅ Micro-segmentation: Zero-trust networking simplified
✅ Full Lifecycle: From development to production security
Next Steps
- 🚀 Deploy test environment with full security enabled
- 📊 Review generated security reports
- 🔧 Tune policies based on your requirements
- ✅ Validate in staging before production
- 📈 Monitor continuous compliance
This document ensures your stacks are secure, compliant, and auditable—with minimal manual effort.